Published CVE numbers:
Headwind MDM Web panel 5.22.1 is vulnerable to Incorrect Access Control. The Web panel allows users to gain access to potentially sensitive API calls such as listing users and their data, file management API calls and audit-related API calls.
Authentication: Required (A low-level user access is enough)
Login to the web panel with the low-level user
By modifying the cookie user so that the superadmin property is set to True, the user interface will show sensitive functions such as user management, file upload, and audit-related functions. These functions are not supposed to be accessible to low-level users. It is important to note that mostly only API calls using GET method can be called this way with the permission of a low-level user. The only exception is the file add function (/rest/private/web-ui-files POST).
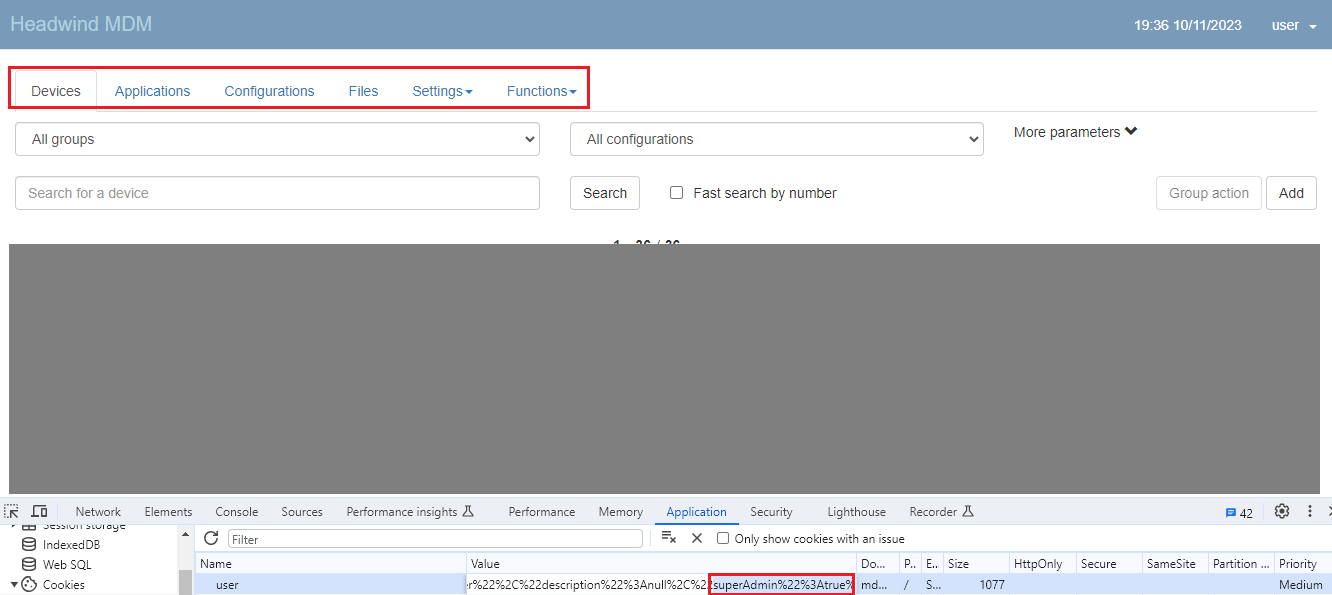
Setting up an attacker proxy like Burp to intercept outgoing HTTP requests and modify them (if it is needed)
By uploading files, attackers may be able to exploit other vulnerabilities; By retrieving the audit function, attackers may learn sensitive information, including login credentials; By retrieving the users’ list, attackers may be able to get the authToken of other users and to get the password reset token (in case the password reset feature is enabled)
Important note: This vulnerability may aid attackers in exploiting other issues, such as CVE-2023-47315, by allowing them to learn the authToken of other users.